Share:
Why mock phishing exercises? They work

If mock phish emails from Asante’s Information Security Team appear to become more difficult to recognize as time goes by, you are right. That’s because real phishes are becoming more difficult to recognize, so our training must keep pace with reality.
The mock phish emails that regularly show up in your mailbox have an important purpose – they remind you of the very real threat of cyberattacks on Asante. If you have been caught by one or more Asante mock phish emails, you most likely learned something about why you were fooled and are less likely to be fooled again.
To shed some light on Asante’s phishing practice exercises, the Information Security Team has prepared the following employee FAQ:
What is the goal of the phishing exercises?
The goal is employee security training and awareness. Asante management and the Information Security Team aim to lessen Asante’s vulnerability to cybercriminal attacks which target our workforce via phishing. When a phish email is recognized and reported by an employee, a cybercriminal’s attempt to maliciously access our computer systems, data or money (ransomware) is likely foiled or lessened.
The Information Security Team is less interested in who clicked on a phish email and who didn’t. Instead, the team wants to learn what phish content is easy to spot by our employees and which is not. In the chart below, it is clear that the mock phish sent in June 2020 was fairly easy for employees to recognize, since 98% of employees recognized the mock phish as a fraud.
More cunning phish emails were sent in June 2021 (posed as HealthStream or Asante News communications); only 90% of employees recognized the fraud. The lesson? Employees need to be reminded that cybercriminals can easily use names and logos of our systems and programs to fool people.
If 10% of 7,000 employees had clicked on a real phish email, at least 700 computers that may have been controlled by cybercriminals. But if 10% of 7,000 employees click on a mock Asante phish email, they may be unhappy, but they are immediately presented with training and a way to recognize such phish emails in the future.
How many phish emails does Asante receive each month?
Asante is targeted by cybercriminals daily — constantly — via email. From July 17 to Aug. 16, 3.9 million emails were delivered to Asante. Of those emails, 3.3 million were deemed invalid or malicious (phish or other malware risk). Ultimately, only 658,000 of the original emails were delivered to staff. However, occasionally some very targeted or well-crafted phish emails make it through our email system’s automated phish filtering process.
Do Asante senior leaders receive phish emails as well as other employees?
Yes. Even our CEO and others in the corporate office receive these emails. And just like the rest of us, some have been fooled by a mock phish email. Since the Asante senior leadership team is especially targeted by cybercriminals, the phish exercises are especially useful for them.
Do Asante leaders pay attention to the outcome of phish exercises?
Yes. The Asante Board of Directors receives a quarterly update on Asante’s employee mock phish campaigns as a part of Asante’s cybersecurity risk report. An employee clicking on a phish email could cripple business operations and patient care services for days, weeks and maybe longer. This could cost the system millions of dollars in lost revenue, fines and other damages.
How are the phishing exercises created and managed?
The Information Security Team uses an automated vendor phishing tool that offers phish email templates, a distribution device and tracking mechanisms. It also offers “post-click” phish training modules for users.
The mock phish emails are timed to arrive in a staggered fashion to improve the chance that an employee has a true opportunity to test their ability to spot and report a phish email to ITS, since co-workers are not likely to receive the same phish at the same time.
The mock phishes are created to mimic real phishes as much as possible. They are often season-appropriate, may pique your curiosity or appeal to your desire to comply with Asante requirements, or mimic other health care or corporate employee concerns.
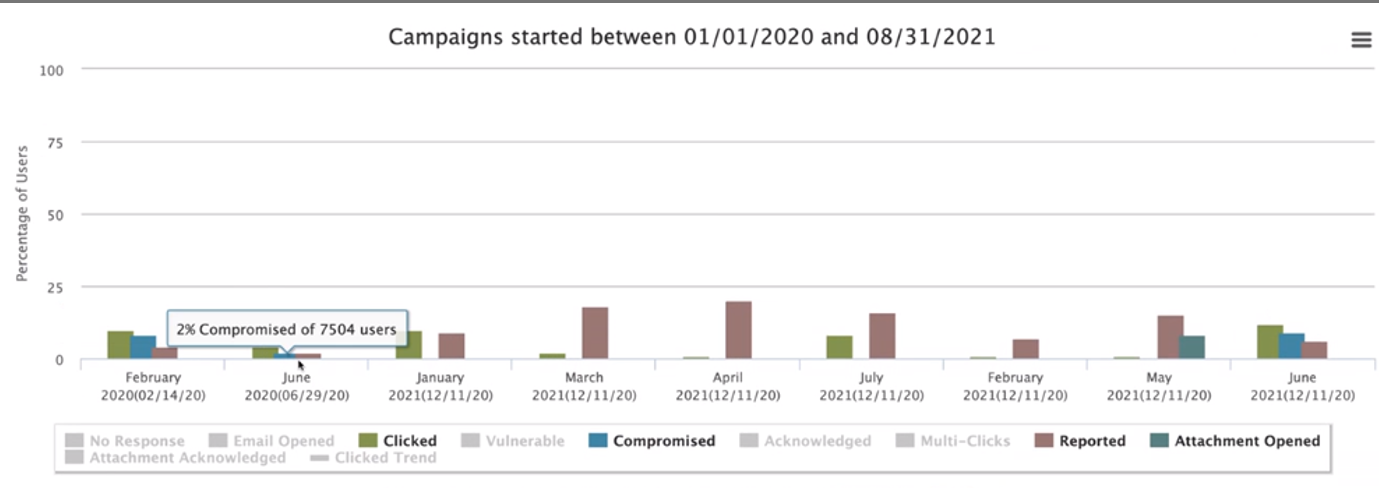
Phish exercise results are automatically calculated by the phishing system and metrics provided to management. The date, time and type of device used to open the phish email is captured, as well as whether:
- The employee clicked on the malicious link or attachment on the email.
- The employee entered their ID and password as part of the phish process.
- The employee reported the phish by clicking the “Report Phish” button.
It is critical that employees use of the “Report Phish” icon (PhishAlarm) on Outlook’s message ribbon when they suspect or click on a phish email since it immediately alerts the Security Team. If the phish is verified as malicious, the phish email is automatically removed from other employees’ mailboxes.
How do employees benefit from the phishing exercise?
If these mock phishing campaigns are frustrating to you, remember: beyond protecting Asante, its patients and employees, the phishing training you receive from Asante will help you avoid falling prey to phish emails to your personal email accounts. When cybercriminals begin “smishing” (phish texts, which are becoming more common) you will have the phish savviness to avoid being caught.
If you have questions or concerns about Asante’s mock phishing exercises, call the ITS Service Desk at (541) 789-4141.
If you have a question, please contact the author or relevant department directly.



4 Comments. Leave new
Thank you for keeping us safe Karen!
You are most welcome; we are all working on this together – since a Human Firewall is needed to thwart cybercrime. Thanks for being a link.
As hard as it is to be fooled, it’s a valuable opportunity to learn. It’s important work and I’m glad we have such diligence in our ranks. Thanks for all you do to protect our system, ITS & Co!!
On behalf of the Security team I can say we are grateful for your understanding of the necessary balance between inconvenience or discomfort VERSUS keeping our vast fleet of computer systems working to support our patients. Thank you!